[New Exam Dumps] What is the Newest Microsoft IT Infrastructure 98-367 Dumps Exam Files And Youtube (Q1-Q40)
What is the newest Microsoft IT Infrastructure 98-367 dumps exam files? Latest Microsoft IT Infrastructure 98-367 dumps pdf files and vce youtube demo update free shared. High quality Microsoft IT Infrastructure 98-367 dumps exam questions and answers free download from geekcert. “MTA Security Fundamentals Practice Test” is the name of Microsoft IT Infrastructure https://www.geekcert.com/98-367.html exam dumps which covers all the knowledge points of the real Microsoft exam. The best and most updated latest Microsoft IT Infrastructure 98-367 dumps exam training resources in PDF format download free try, pass Microsoft 98-367 exam test quickly and easily.
High quality Microsoft IT Infrastructure 98-367 dumps pdf practice files and study guides free download from geekcert. Helpful newest Microsoft IT Infrastructure 98-367 dumps exam is omnipresent all around the world, and the business and software solutions provided by them are being embraced by almost all the companies. 100% success and guarantee to pass Microsoft 98-367 exam.

Best Microsoft IT Infrastructure 98-367 Dumps Exam Questions And Answers (1-40)
QUESTION 1
What is the primary advantage of using Active Directory Integrated Zones?
A. Zone encryption
B. Password protection
C. Non-repudiation
D. Secure replication
Correct Answer: D
QUESTION 2
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

Hot Area:

Correct Answer:
QUESTION 3
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

Hot Area:

Correct Answer:
QUESTION 4
What is a service set identifier (SSID)?
A. A wireless encryption standard
B. The wireless LAN transmission type
C. The broadcast name of an access point
D. A wireless security protocol
Correct Answer: C
QUESTION 5
Alice and Bob are exchanging messages with each other. 98-367 dumps Chuck modifies the messages sent between Alice and Bob as shown in the following image:

Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.

Hot Area:

Correct Answer:

QUESTION 6
You are an intern at Litware, Inc. Your manager asks you to make password guess attempts harder by limiting login attempts on company computers.
What should you do?
A. Enforce password sniffing.
B. Enforce password history.
C. Make password complexity requirements higher.
D. Implement account lockout policy.
Correct Answer: D
QUESTION 7
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

Hot Area:

Correct Answer:

QUESTION 8
A user who receives a large number of emails selling prescription medicine is probably receiving pharming mail.
Select the correct answer if the underlined text does not make the statement correct. Select andquot;No change is neededandquot; if the underlined text makes the statement correct.
A. Malware
B. Spoofed mail
C. Spam
D. No change is needed.
Correct Answer: C
QUESTION 9
Which is a special folder permission?
A. Read
B. Modify
C. Write
D. Delete
Correct Answer: D
QUESTION 10
The purpose of a digital certificate is to verify that a:
A. Public key belongs to a sender.
B. Computer is virus-free.
C. Private key belongs to a sender.
D. Digital document is complete.
Correct Answer: A
QUESTION 11
Password history policies are used to prevent:
A. Brute force attacks
B. Users from sharing passwords
C. Social engineering
D. Passwords from being reused immediately
Correct Answer: D
QUESTION 12
You need to install a domain controller in a branch office. You also need to secure the information on the domain controller. You will be unable to physically secure the server. 98-367 dumps
Which should you implement?
A. Read-Only Domain Controller
B. Point-to-Point Tunneling Protocol (PPTP)
C. Layer 2 Tunneling Protocol (L2TP)
D. Server Core Domain Controller
Correct Answer: A
QUESTION 13
To protect systems from buffer overflow errors, you can use:
A. Antivirus software
B. Data Execution Prevention
C. A proxy server
D. An Intruder Prevention System
Correct Answer: B
QUESTION 14
The default password length for a Windows Server domain controller is:
A. 0
B. 5
C. 7
D. 14
Correct Answer: C
QUESTION 15
Cookies impact security by enabling: (Choose two.)
A. Storage of Web site passwords.
B. Higher security Web site protections.
C. Secure Sockets Layer (SSL).
D. Web sites to track browsing habits.
Correct Answer: AD
QUESTION 16
A brute force attack:
A. Uses response filtering
B. Tries all possible password variations
C. Uses the strongest possible algorithms
D. Targets all the ports
Correct Answer: B
QUESTION 17
Before you deploy Network Access Protection (NAP), you must install:
A. Internet Information Server (IIS)
B. Network Policy Server (NPS)
C. Active Directory Federation Services
D. Windows Update Service
Correct Answer: B
QUESTION 18
You suspect a user\’s computer is infected by a virus. What should you do first?
A. Restart the computer in safe mode
B. Replace the computer\’s hard disk drive
C. Disconnect the computer from the network
D. Install antivirus software on the computer
Correct Answer: D
QUESTION 19
You need to prevent unauthorized users from reading a specific file on a portable computer if the portable computer is stolen. What should you implement?
A. File-level permissions
B. Advanced Encryption Standard (AES)
C. Folder-level permissions
D. Distributed File System (DFS)
E. BitLocker
Correct Answer: E
QUESTION 20
You have a Windows 7 desktop computer, and you create a Standard User account for your roommate so that he can use the desktop from time to time. Your roommate has forgotten his password.
Which two actions can you take to reset the password? (Choose two.)
A. Use your password reset disk.
B. Use your administrator account.
C. Boot into Safe Mode with your roommate\’s account.
D. From your roommate\’s account press CTRL+ALT+DELETE, and then click Change a password.
Correct Answer: AB
QUESTION 21
In Internet Explorer 8, the InPrivate Browsing feature prevents:
A. Unauthorized private data input.
B. Unencrypted communication between the client computer and the server.
C. User credentials from being sent over the Internet.
D. Any session data from being stored on the computer.
Correct Answer: D
QUESTION 22
Your supervisor asks you to review file permission settings on the application.bat file. You need to report which file system the file is on and the type of permission the file has. 98-367 dumps You review the application Properties dialog box shown in the following image: Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
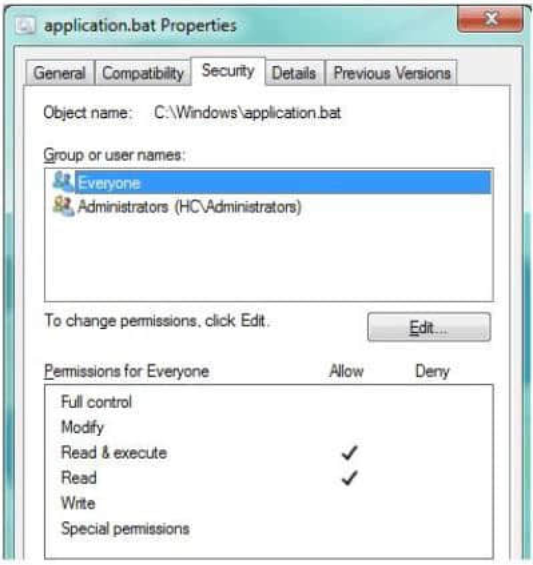

Hot Area:

Correct Answer:
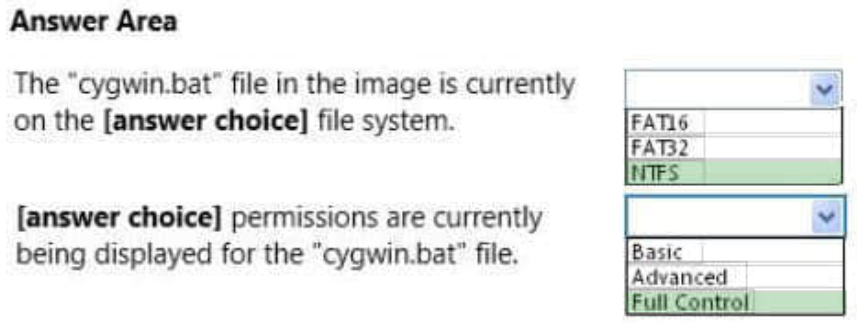
QUESTION 23
Which type of firewall allows for inspection of all characteristics of a packet?
A. NAT
B. Stateful
C. Stateless
D. Windows Defender
Correct Answer: B
QUESTION 24
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

Hot Area:

Correct Answer:

QUESTION 25
Which provides the highest level of security in a firewall?
A. Stateful inspection
B. Outbound packet filters
C. Stateless inspection
D. Inbound packet filters
Correct Answer: A
QUESTION 26
Passwords that contain recognizable words are vulnerable to a:
A. Denial of Service attack
B. Hashing attack
C. Dictionary attack
D. Replay attack
Correct Answer: C
QUESTION 27
Humongous Insurance is an online healthcare insurance company. During an annual security audit a security firm tests the strength of the company\’s password policy and suggests that Humongous Insurance implement password history policy.
What is the likely reason that the security firm suggests this?
A. Past passwords were easily cracked by the brute force method.
B. Past passwords of users contained dictionary words.
C. Previous password breaches involved use of past passwords.
D. Past passwords lacked complexity and special characters.
Correct Answer: B
QUESTION 28
You are trying to establish communications between a client computer and a server. The server is not responding.
You confirm that both the client and the server have network connectivity.
Which should you check next?
A. Microsoft Update
B. Data Execution Prevention
C. Windows Firewall
D. Active Directory Domains and Trusts
Correct Answer: D
QUESTION 29
Coho Winery wants to increase their web presence and hires you to set up a new web server. Coho already has servers for their business and would like to avoid purchasing a new one.
Which server is best to use as a web server, considering the security and performance concerns?
A. SQL Server
B. File Server
C. Domain Controller
D. Application Server
Correct Answer: C
QUESTION 30
Which password attack uses all possible alpha numeric combinations?
A. Social engineering
B. Brute force attack
C. Dictionary attack
D. Rainbow table attack
Correct Answer: C
QUESTION 31
Humongous Insurance needs to set up a domain controller in a branch office. Unfortunately, the server cannot be sufficiently secured from access by employees in that office, so the company is installing a Primary Domain Controller.
Select the correct answer if the underlined text does not make the statement correct. Select andquot;No change is neededandquot; if the underlined text makes the statement correct.
A. Read-Only Domain Controller
B. Backup Domain Controller
C. Active Directory Server
D. No change is needed.
Correct Answer: A
QUESTION 32
What does implementing Windows Server Update Services (WSUS) allow a company to manage?
A. Shared private encryption key updates
B. Updates to Group Policy Objects
C. Active Directory server replication
D. Windows updates for workstations and servers
Correct Answer: D
QUESTION 33
You need to limit the programs that can run on client computers to a specific list. 98-367 dumps Which technology should you implement?
A. Windows Security Center
B. Security Accounts Manager
C. System Configuration Utility
D. AppLocker group policies
Correct Answer: A
QUESTION 34
To prevent users from copying data to removable media, you should:
A. Lock the computer cases
B. Apply a group policy
C. Disable copy and paste
D. Store media in a locked room
Correct Answer: B
QUESTION 35
Many Internet sites that you visit require a user name and password. How should you secure these passwords?
A. Save them to a text file
B. Enable session caching
C. Configure the browser to save passwords
D. Save them to an encrypted file
E. Reuse the same password
Correct Answer: D
QUESTION 36
What are three major attack vectors that a social engineering hacker may use? (Choose three.)
A. Telephone
B. Reverse social engineering
C. Waste management
D. Honey pot systems
E. Firewall interface
Correct Answer: ABC
QUESTION 37
You have two servers that run Windows Server. All drives on both servers are formatted by using NTFS. You move a file from one server to the other server. The file\’s permissions in the new location will:
A. Enable full access to the everyone group
B. Restrict access to the Administrators group
C. Inherit the destination folder\’s permissions
D. Retain the original folder\’s permissions
Correct Answer: C
QUESTION 38
Windows Server Update Services (WSUS) is a tool that:
A. Updates data stored in Windows servers
B. Manages the services that run on a server
C. Updates licensing for Windows servers
D. Manages updates for Microsoft software
Correct Answer: D
QUESTION 39
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

Hot Area:

Correct Answer:

QUESTION 40
The Active Directory controls, enforces, and assigns security policies and access rights for all users. Select the correct answer if the underlined text does not make the statement correct. Select andquot;No change is neededandquot; if the underlined text makes the statement correct.
A. NTFS permissions
B. User Account Control
C. Registry
D. No change is needed
Correct Answer: D
Here Are Some Reviews From Our Customers:

Latest Microsoft 98-367 dumps pdf practice files: https://drive.google.com/open?id=1ZnYRM1_-dFlLOqH9i0af1z-yO8kXUACy
Latest Microsoft 98-365 dumps pdf practice files: https://drive.google.com/open?id=1OAmgeotOwsFKS7zxOfZh6EhlqKWlGNJr

Helpful latest Microsoft IT Infrastructure 98-367 dumps pdf practice materials and study guides free download from geekcert. New Microsoft IT Infrastructure https://www.geekcert.com/98-367.html dumps pdf training resources which are the best for clearing 98-367 exam test, and to get certified by Microsoft Microsoft IT Infrastructure, download one of the many PDF readers that are available for free with high pass rate.
Why Select Lead 4 Pass?
geekcert is the best IT learning material provider. Other brands appeared early, the questions are not the latest and it is very expensive. geekcert provide the newest and cheapest questions and answers. geekcert is the correct choice for IT learning materials, help you pass your exam easily.


