2018 new EC-COUNCIL CCISO 712-50 dumps exam practice materials in PDF format free download from lead4pass. Useful latest EC-COUNCIL CCISO 712-50 dumps vce youtube demo update free shared. “EC-Council Certified CISO (CCISO)” is the name of EC-COUNCIL CCISO https://www.leads4pass.com/712-50.html exam dumps which covers all the knowledge points of the real EC-COUNCIL exam. Latest EC-COUNCIL CCISO 712-50 dumps exam questions and answers free download, 100% success and guarantee to pass EC-COUNCIL CCISO 712-50 exam test easily.
Helpful latest EC-COUNCIL CCISO 712-50 dumps pdf training resources download free try. The best and most updated latest EC-COUNCIL CCISO 712-50 dumps exam is the industry leader in information technology, and getting certified by them is a guaranteed way to succeed with IT careers. It is the best choice for you to pass EC-COUNCIL CCISO 712-50 exam test.

Best EC-COUNCIL CCISO 712-50 Dumps Exam Questions And Answers (1-30)
QUESTION 1
When dealing with risk, the information security practitioner may choose to:
A. assign
B. transfer
C. acknowledge
D. defer
Correct Answer: C
QUESTION 2
According to the National Institute of Standards and Technology (NIST) SP 800-40, which of the following considerations are MOST important when creating a vulnerability management program?
A. Susceptibility to attack, mitigation response time, and cost
B. Attack vectors, controls cost, and investigation staffing needs
C. Vulnerability exploitation, attack recovery, and mean time to repair
D. Susceptibility to attack, expected duration of attack, and mitigation availability
Correct Answer: A
QUESTION 3
Acme Inc. has engaged a third party vendor to provide 99.999% up-time for their online web presence and had them contractually agree to this service level agreement. What type of risk tolerance is Acme exhibiting? (choose the BEST answer):
A. low risk-tolerance
B. high risk-tolerance
C. moderate risk-tolerance
D. medium-high risk-tolerance
Correct Answer: A
QUESTION 4
Which of the following is a major benefit of applying risk levels?
A. Risk management governance becomes easier since most risks remain low once mitigated
B. Resources are not wasted on risks that are already managed to an acceptable level
C. Risk budgets are more easily managed due to fewer identified risks as a result of using a methodology
D. Risk appetite can increase within the organization once the levels are understood
Correct Answer: B
QUESTION 5
To get an Information Security project back on schedule, 712-50 dumps which of the following will provide the MOST help?
A. Upper management support
B. More frequent project milestone meetings
C. Stakeholder support
D. Extend work hours
Correct Answer: A
QUESTION 6
The process to evaluate the technical and non-technical security controls of an IT system to validate that a given design and implementation meet a specific set of security requirements is called
A. Security certification
B. Security system analysis
C. Security accreditation
D. Alignment with business practices and goals.
Correct Answer: A
QUESTION 7
When managing the security architecture for your company you must consider:
A. Security and IT Staff size
B. Company Values
C. Budget
D. All of the above
Correct Answer: D
QUESTION 8
Which of the following is a term related to risk management that represents the estimated frequency at which a threat is expected to transpire?
A. Single Loss Expectancy (SLE)
B. Exposure Factor (EF)
C. Annualized Rate of Occurrence (ARO)
D. Temporal Probability (TP)
Correct Answer: C
QUESTION 9
You have recently drafted a revised information security policy. From whom should you seek endorsement in order to have the GREATEST chance for adoption and implementation throughout the entire organization?
A. Chief Information Security Officer
B. Chief Executive Officer
C. Chief Information Officer
D. Chief Legal Counsel
Correct Answer: B
QUESTION 10
Scenario: Your organization employs single sign-on (user name and password only) as a convenience to your employees to access organizational systems and data. Permission to individual systems and databases is vetted and approved through supervisors and data owners to ensure that only approved personnel can use particular applications or retrieve information. All employees have access to their own human resource information, including the ability to change their bank routing and account information and other personal details through the Employee Self-Service application. All employees have access to the organizational VPN.
What type of control is being implemented by supervisors and data owners?
A. Management
B. Operational
C. Technical
D. Administrative
Correct Answer: B
QUESTION 11
You manage a newly created Security Operations Center (SOC), your team is being inundated with security alerts and don\’t know what to do. What is the BEST approach to handle this situation?
A. Tell the team to do their best and respond to each alert
B. Tune the sensors to help reduce false positives so the team can react better
C. Request additional resources to handle the workload
D. Tell the team to only respond to the critical and high alerts
Correct Answer: B
QUESTION 12
Within an organization\’s vulnerability management program, who has the responsibility to implement remediation actions?
A. Security officer
B. Data owner
C. Vulnerability engineer
D. System administrator
Correct Answer: D
QUESTION 13
Scenario: Most industries require compliance with multiple government regulations and/or industry standards to meet data protection and privacy mandates. When multiple regulations or standards apply to your industry you should set controls to meet the:
A. Easiest regulation or standard to implement
B. Stricter regulation or standard
C. Most complex standard to implement
D. Recommendations of your Legal Staff
Correct Answer: A
QUESTION 14
When dealing with Security Incident Response procedures, 712-50 dumps which of the following steps come FIRST when reacting to an incident?
A. Escalation
B. Recovery
C. Eradication
D. Containment
Correct Answer: D
QUESTION 15
Which of the following is a weakness of an asset or group of assets that can be exploited by one or more threats?
A. Threat
B. Vulnerability
C. Attack vector
D. Exploitation
Correct Answer: B
QUESTION 16
What are the primary reasons for the development of a business case for a security project?
A. To estimate risk and negate liability to the company
B. To understand the attack vectors and attack sources
C. To communicate risk and forecast resource needs
D. To forecast usage and cost per software licensing
Correct Answer: C
QUESTION 17
An organization is required to implement background checks on all employees with access to databases containing credit card information. This is considered a security
A. Procedural control
B. Management control
C. Technical control
D. Administrative control
Correct Answer: B
QUESTION 18
Scenario: Your program is developed around minimizing risk to information by focusing on people, technology, and operations.
An effective way to evaluate the effectiveness of an information security awareness program for end users, especially senior executives, is to conduct periodic:
A. Controlled spear phishing campaigns
B. Password changes
C. Baselining of computer systems
D. Scanning for viruses
Correct Answer: A
QUESTION 19
SQL injection is a very popular and successful injection attack method. Identify the basic SQL injection text:
A. ` o 1=1 –
B. /../../../../
C. andquot;DROPTABLE USERNAMEandquot;
D. NOPS
Correct Answer: A
QUESTION 20
When measuring the effectiveness of an Information Security Management System which one of the following would be MOST LIKELY used as a metric framework?
A. ISO 27001
B. PRINCE2
C. ISO 27004
D. ITILv3
Correct Answer: C
QUESTION 21
An organization has defined a set of standard security controls. This organization has also defined the circumstances and conditions in which they must be applied. What is the NEXT logical step in applying the controls in the organization?
A. Determine the risk tolerance
B. Perform an asset classification
C. Create an architecture gap analysis
D. Analyze existing controls on systems
Correct Answer: B
QUESTION 22
The risk found after a control has been fully implemented is called:
A. Residual Risk
B. Total Risk
C. Post implementation risk
D. Transferred risk
Correct Answer: A
QUESTION 23
SCENARIO: A Chief Information Security Officer (CISO) recently had a third party conduct an audit of the security program. Internal policies and international standards were used as audit baselines. The audit report was presented to the CISO and a variety of high, medium and low rated gaps were identified.
The CISO has implemented remediation activities. Which of the following is the MOST logical next step?
A. Validate the effectiveness of applied controls
B. Validate security program resource requirements
C. Report the audit findings and remediation status to business stake holders
D. Review security procedures to determine if they need modified according to findings
Correct Answer: A
QUESTION 24
Scenario: Your organization employs single sign-on (user name and password only) as a convenience to your employees to access organizational systems and data. Permission to individual systems and databases is vetted and approved through supervisors and data owners to ensure that only approved personnel can use particular applications or retrieve information. 712-50 dumps All employees have access to their own human resource information, including the ability to change their bank routing and account information and other personal details through the Employee Self-Service application. All employees have access to the organizational VPN.
Recently, members of your organization have been targeted through a number of sophisticated phishing attempts and have compromised their system credentials. What action can you take to prevent the misuse of compromised credentials to change bank account information from outside your organization while still allowing employees to manage their bank information?
A. Turn off VPN access for users originating from outside the country
B. Enable monitoring on the VPN for suspicious activity
C. Force a change of all passwords
D. Block access to the Employee-Self Service application via VPN
Correct Answer: D
QUESTION 25
Which of the following BEST describes an international standard framework that is based on the security model Information Technology–Code of Practice for Information Security Management?
A. International Organization for Standardization 27001
B. National Institute of Standards and Technology Special Publication SP 800-12
C. Request For Comment 2196
D. National Institute of Standards and Technology Special Publication SP 800-26
Correct Answer: A
QUESTION 26
A system was hardened at the Operating System level and placed into the production environment. Months later an audit was performed and it identified insecure configuration different from the original hardened state. Which of the following security issues is the MOST likely reason leading to the audit findings?
A. Lack of asset management processes
B. Lack of change management processes
C. Lack of hardening standards
D. Lack of proper access controls
Correct Answer: B
QUESTION 27
The FIRST step in establishing a security governance program is to?
A. Conduct a risk assessment.
B. Obtain senior level sponsorship.
C. Conduct a workshop for all end users.
D. Prepare a security budget.
Correct Answer: B
QUESTION 28
The Security Operations Center (SOC) just purchased a new intrusion prevention system (IPS) that needs to be deployed in-line for best defense. The IT group is concerned about putting the new IPS in-line because it might negatively impact network availability. What would be the BEST approach for the CISO to reassure the IT group?
A. Work with the IT group and tell them to put IPS in-line and say it won\’t cause any network impact
B. Explain to the IT group that the IPS won\’t cause any network impact because it will fail open
C. Explain to the IT group that this is a business need and the IPS will fail open however, if there is a network failure the CISO will accept responsibility
D. Explain to the IT group that the IPS will fail open once in-line however it will be deployed in monitor mode for a set period of time to ensure that it doesn\’t block any legitimate traffic
Correct Answer: D
QUESTION 29
A business unit within your organization intends to deploy a new technology in a manner that places it in violation of existing information security standards. What immediate action should the information security manager take?
A. Enforce the existing security standards and do not allow the deployment of the new technology.
B. Amend the standard to permit the deployment.
C. If the risks associated with that technology are not already identified, perform a risk analysis to quantify the risk, and allow the business unit to proceed based on the identified risk level.
D. Permit a 90-day window to see if an issue occurs and then amend the standard if there are no issues.
Correct Answer: C
QUESTION 30
Scenario: You are the CISO and have just completed your first risk assessment for your organization. You find many risks with no security controls, and some risks with inadequate controls. You assign work to your staff to create or adjust existing security controls to ensure they are adequate for risk mitigation needs.
When adjusting the controls to mitigate the risks, how often should the CISO perform an audit to verify the controls?
A. Annually
B. Semi-annually
C. Quarterly
D. Never
Correct Answer: D
The Following Are Some Reviews From Our Customers:

Useful EC-COUNCIL CCISO 712-50 dumps pdf practice materials: https://drive.google.com/open?id=1jXRPn_Gx9Aa-BUwKyEZPVDEpZnVFykv9
Useful Microsoft 70-462 dumps pdf practice materials: https://drive.google.com/open?id=18sajc7KUFskDJCCTyWm57OUSXHJKMDBX
The best and most updated latest EC-COUNCIL CCISO 712-50 dumps pdf practice files and study guides free download from lead4pass. High quality EC-COUNCIL CCISO https://www.leads4pass.com/712-50.html dumps pdf training resources which are the best for clearing 712-50 exam test, and to get certified by EC-COUNCIL CCISO, download one of the many PDF readers that are available for free.
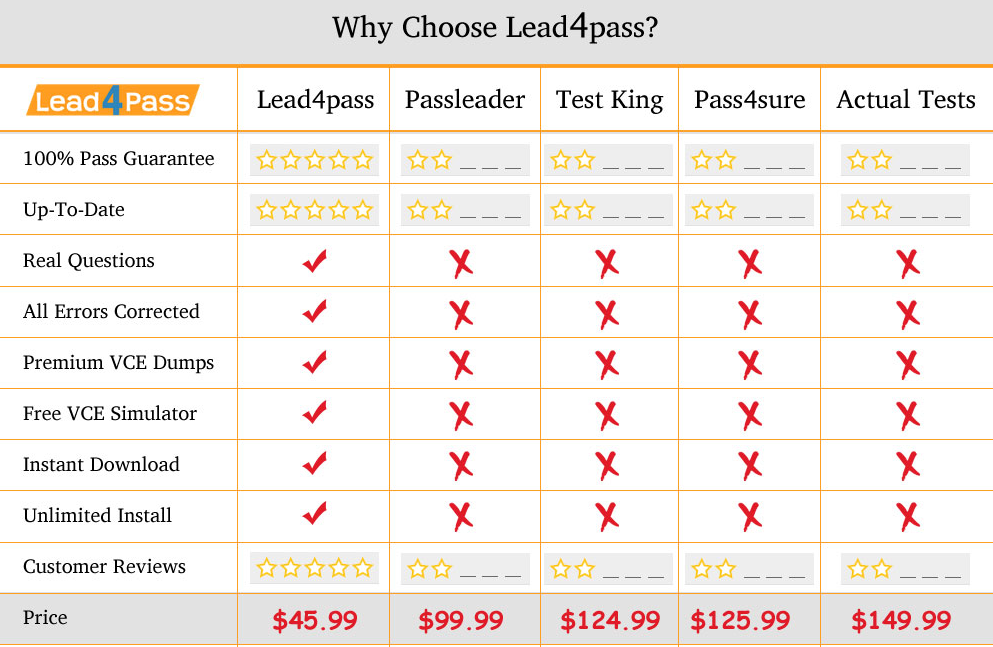
Why Choose Lead4pass?
Lead4pass is the best provider of IT learning materials and the right choice for you to pass the exam. Other brands started earlier, but the questions are not the newest the price is relatively expensive. Lead4pass provide the latest real and cheapest questions and answers, help you pass the exam easily at first try.